Sherlock Scenario
You are a junior threat intelligence analyst at a Cybersecurity firm. You have been tasked with investigating a Cyber espionage campaign known as Operation Dream Job. The goal is to gather crucial information about this operation.
- Who conducted Operation Dream Job? Lazarus Group
- Reviewed attack.mitre.org and searched for Operation Dream Job.

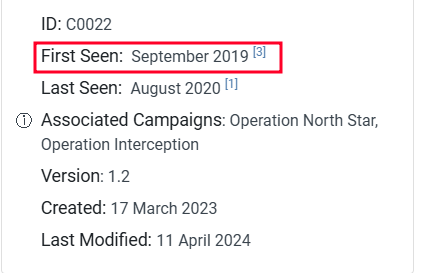
- When was this operation first observed? September 2019
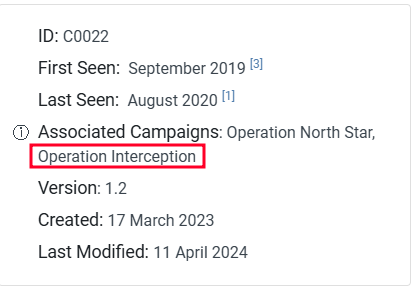
- There are 2 campaigns associated with Operation Dream Job. One is
Operation North Star, what is the other? Operation Interception
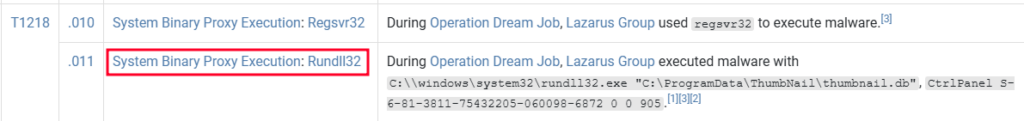
- During Operation Dream Job, there were the two system binaries used for proxy execution. One was
Regsvr32, what was the other? Rundll32
- Reading through the techniques used you will find two binary executions Regsvr32 and Rundll32.
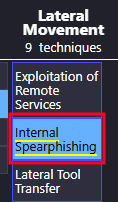
- What lateral movement technique did the adversary use? Internal Spearphishing
- In ATT&CK Navigator Layers open the view and under Lateral Movement you will see 9 techniques and Internal Spearphishing was used.
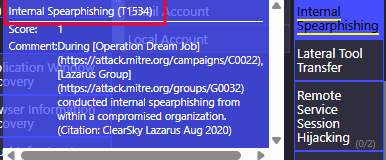
- What is the technique ID for the previous answer? T1534
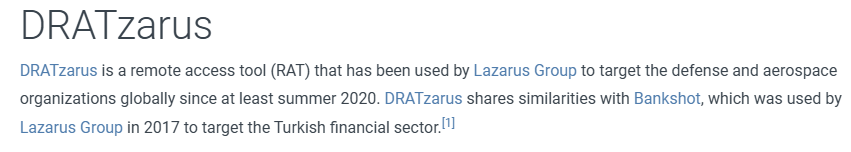
- What Remote Access Trojan did the Lazarus Group use in Operation Dream Job? DRATzarus
- Reading through the MITRE ATT&CK you find under software the tool used.
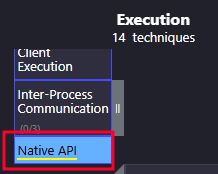
- What technique did the malware use for execution? Native API
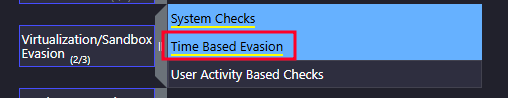
- What technique did the malware use to avoid detection in a sandbox? Time Based Evasion
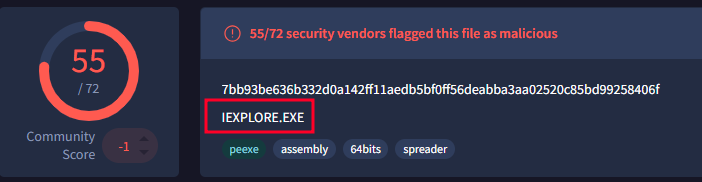
- To answer the remaining questions, utilize VirusTotal and refer to the IOCs.txt file. What is the name associated with the first hash provided in the IOC file? IEXPLORE.exe
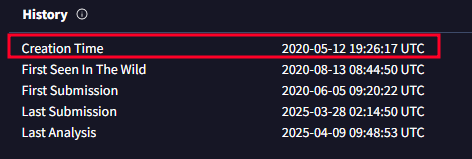
- When was the file associated with the second hash in the IOC first created? 2020-05-12 19:26:17
- In VirusTotal under the DETAILS section you will see the history of the file.
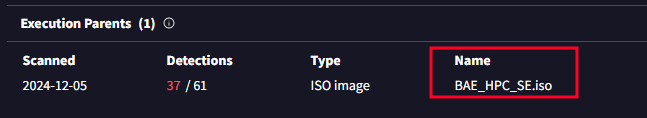
- What is the name of the parent execution file associated with the second hash in the IOC? BAE_HPC_SE.iso
- In VirusTotal under the RELATIONS section you will find Execution Parents.
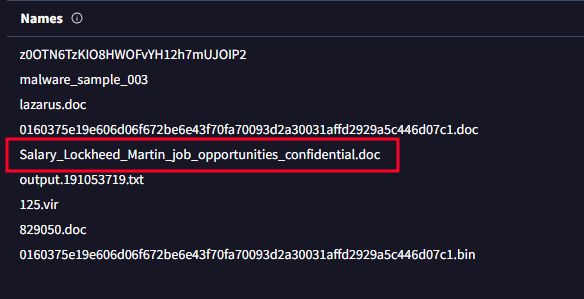
- Examine the third hash provided. What is the file name likely used in the campaign that aligns with the adversary’s known
tactics? Salary_Lockheed_Martin_job_opportunities_confidential.doc
After reviewing the has in VirusTotal you see under the DETAILS section the name of the file used.
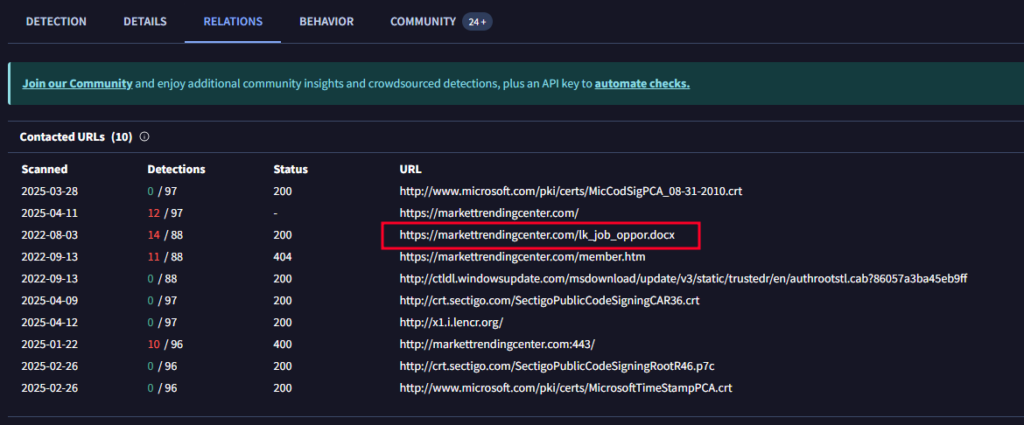
- Which URL was contacted on 2022-08-03 by the file associated with the third hash in the IOC
**file? https://markettrendingcenter.com/lk_job_oppor.docx**
In VirusTotal under the RELATIONS section you will see the URL related to jobs which matches this attack.